This article is a service message from Exceed Consulting regarding a recent widespread virus outbreak.
Cryptolocker Virus Alert
A major virus threat has started making the rounds. Typically the virus is introduced by email. In this case, the emails are often, but not always, just text with no (or very few) links and a single attachment. Typically the attachment is in a .zip format with a single file inside. The file inside is an infection program but appears to be a pdf. This malicious payload can be especially difficult to distinguish as a .exe if file extensions are not visible to the user.
Please continue below to view the general methods for avoiding infection provided after this alert example.
How Cryptolocker Gets In
Information regarding the Cryptolocker virus. The key features & payload of this virus, more generally called malware, are that it typically installs by opening an email attachment disguised as an invoice in a zip or pdf format. Many antivirus tools are still unable to detect this virus effectively, and most web filtering is only able to block a small portion of the compromised web addresses.
What Cryptolocker Does
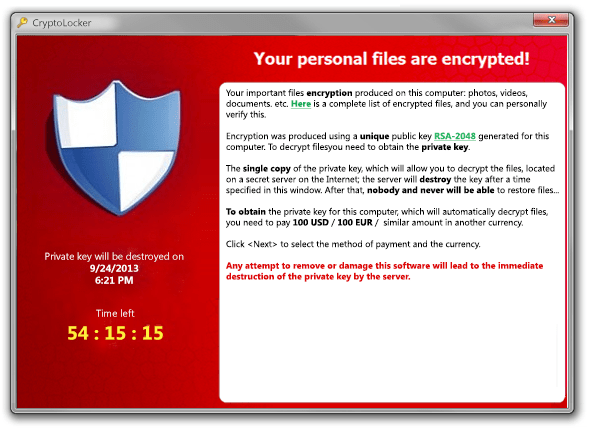
The virus payload encrypts all of your documents in local and shared storage (Word, Excel, PowerPoint, AutoCAD drawings, Photos, etc.) with 2048-bit encryption.
The virus can infect and encrypt both local and network-attached storage. Read this as ANY storage the user has access to while logged into the infected desktop, laptop, server, remote desktop, or Citrix session.
The virus then ransoms your files for 100 hours at $300 or more to decrypt them.
Following the deadline or early termination by removing the virus, the ransom increases to at least $2000, and the threat actors require sending sample files to retrieve the decryption key.
There is, of course, absolutely no obligation by the criminals to release the decryption key to the infected party.
How to Remove CryptoLocker and Repair the Damage, and Prevent where Possible
The virus can be stopped and removed relatively quickly since it is typically only one to a few files. However, once the 2048-bit encryption of files has occurred, rolling back to a pre-infected snapshot or backup is the only method to recover infected files.
The ransom must often be paid in cryptocurrency, typically Bitcoin, when working with the threat actors to pay the ransom and recover the encrypted files. Threat actors use cryptocurrencies to make the ransoms untraceable.
More information and sources
http://en.wikipedia.org/wiki/CryptoLocker
http://krebsonsecurity.com/2013/11/how-to-avoid-cryptolocker-ransomware
CryptoLocker Is The Nastiest Malware Ever & Here’s What You Can Do
Matthew Hughes (Oct 29, 2013)
The CryptoPrevent utility from Foolish IT may prevent infection at the desktop level.
http://www.foolishIT.com/vb6-projects/cryptoprevent/
Unfortunately, if you see a cryptovirus running on your desktop, CryptoPrevent can’t reverse the process.
Related Article: 10 tips to stop viruses and malware on your computer
