From risk to resilience
Elevate your network with EDR, Protected Network strategies, and Zero Trust Architecture.
Protecting your network is no longer a simple checklist; it’s necessary in today’s digital landscape. Explore the journey from an unprotected network to a robust, secure infrastructure.
The benefits of a protected network are undeniable. Shielding your cloud services and remote users with cutting-edge email protection, zero trust architecture, and comprehensive threat detection and response solutions empowers you to:
- Prevent unauthorized access and data leaks
- Detect and respond to threats in real-time
- Ensure compliance with industry regulations
- Maintain business continuity in the face of attacks
- Gain peace of mind and focus on driving innovation
Don’t let your network be the weak link in your security chain. Upgrade to a protected network today. Your organization, your customers, and your bottom line will thank you.
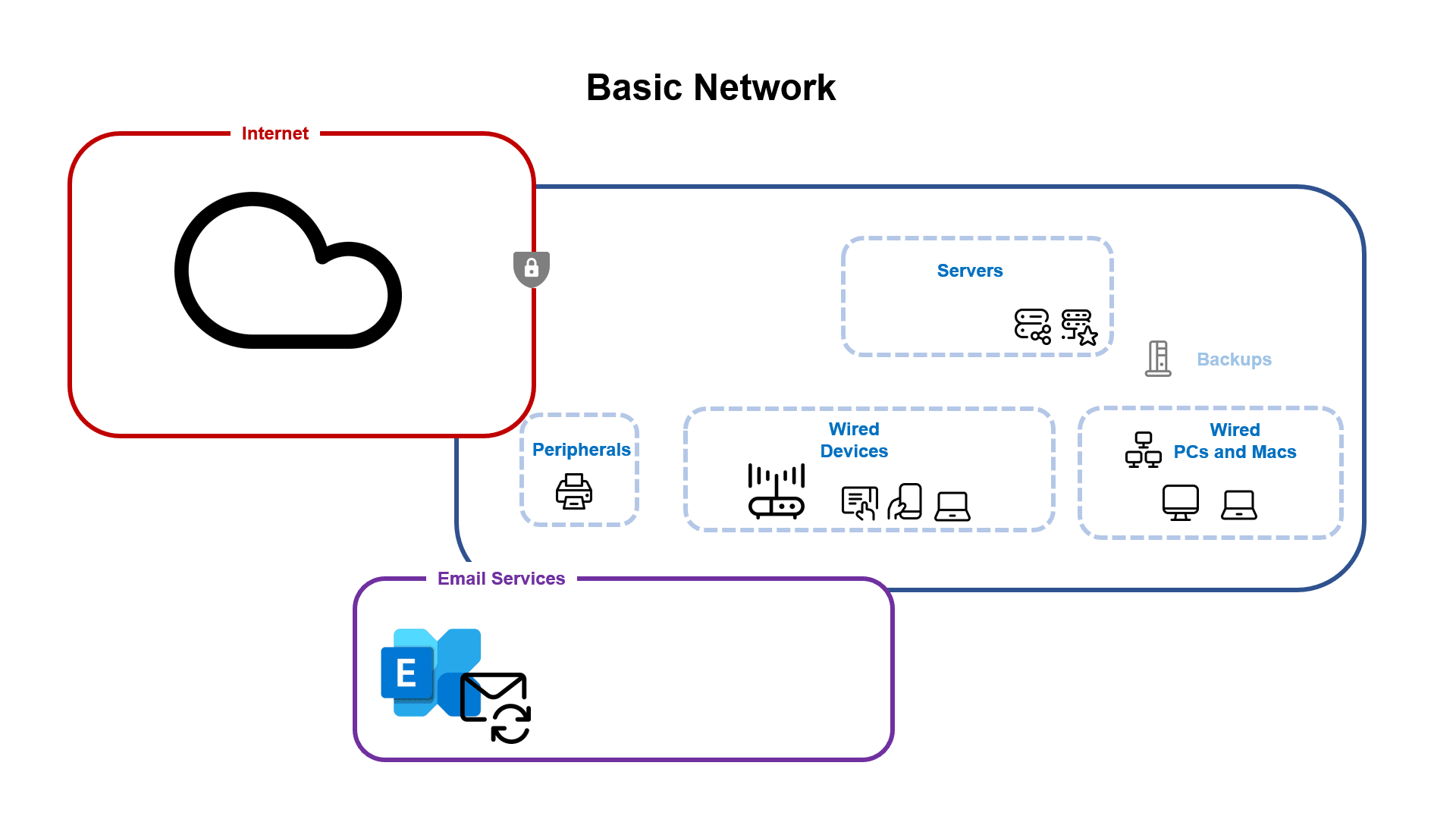
Intermediate Network
You’ve started adding cloud services. Some of your users are starting to work from home or while traveling to customer sites, and your server footprint is growing.
Next, you contact Exceed Consulting for assistance and planning. We work with you to define licensing for a dedicated email service and discuss ways to protect your investment with a good backup solution.
AV
Antivirus
Traditional Antivirus
Uses a virus ‘signature’ database to detect viruses
Without a central management console, updates are performed on a predefined schedule
NGAV
Next Generation Antivirus
Advanced real-time scanning with a personal firewall.
Centralized management console, sometimes with cloud-based management.
Updates are pushed to antivirus software on-demand to protect against zero-day threats.
EPP
Endpoint Protection
Protects systems on and off the network with real-time management, firewall, and web filtering.
Cloud-based real-time management console with alerting.
Updates are pushed to clients on and off the business network.
Advanced Network
Exceed Consulting is the premier partner that can assist your organization in seamlessly migrating on-premise services and infrastructure to cloud-based solutions. As the workplace landscape continues to evolve, with more employees transitioning to a hybrid or fully remote work model, Exceed Consulting can help you navigate this shift. By transitioning your email communication to a dedicated cloud-based service, your workforce will benefit from enhanced storage capabilities, advanced collaboration features, and improved reliability. Moreover, Exceed Consulting has ensured that your systems are fortified with robust antivirus protection, safeguarding your PCs, servers, and critical data against the ever-present threats of malware, ransomware, and other malicious cyberattacks. With Exceed Consulting as your reliable partner, you can confidently embrace the benefits of cloud computing and remote work while maintaining the highest levels of security and productivity.
IDS
Intrusion Detection System
Rules-based detection.
Some automated updates and provides alerting.
Reactive detection against active threats.
EDR
Endpoint Detection & Response
Advanced real-time scanning and monitoring of business networks.
Performs threat analyses against business resources based on behavior detection.
Predictive response to threats and malware.
XDR
Extended Detection & Response
Advanced real-time scanning and monitoring of business networks and cloud assets. Additional perimeter and cloud protection to behavior protection provided for your business.
Predictive response to threats and malware on-premise and in the cloud.
Basic Protection
But wait, isn’t antivirus protection? It was many years ago. The fact is that threats and threat responses are an evolving arms race with new variants and challenges every day. You have embraced cloud services, and hybrid workers have become full-time remote workers. You also need full backups of critical systems and your dedicated email and communications platform. You decided to secure your network from inbound threats with a Barracuda CloudGen Firewall provided by Exceed. Through a VPN, your remote workers can directly connect to your network. To manage these solutions effectively, you signed a management agreement with Exceed.
FW
Firewall
Rules based protection.
Protects against basic threats not aware of application or context-driven traffic.
VPN capabilities.
NGFW
Next Generation Firewall
Capable of virus detection at the network perimeter even within secure transfers.
Application awareness, Intrusion detection.
Provides deep packet inspection and intrusion detection to gain context.
CGFW
Cloud Generation Firewall
Capable of cloud-based or centralized management.
Can be installed in many cloud services.
Provides site-to-site and site-to-cloud VPN protection.
Intermediate Protection
Exceed works with you to implement a dedicated remote work solution through an SSL-protected solution like Parallels or Citrix. Company resources provide a physical layer of protection between remote user systems and your network perimeter. To protect your email, cloud storage, and online communications within Microsoft Office 365, Exceed Consulting helps you add Barracuda Email Protection.
The Email Security Gateway (required) offers advanced anti-spam protection and state-of-the-art AI to protect you from most email threats.
Impersonation Protection (required) provides added protection against infiltration and phishing attacks through active AI-based monitoring of mailbox activities, such as rule changes and emails that look “fishy.” End-users can easily retrieve messages by implementing a cloud-to-cloud email archiver. Cloud-to-Cloud Backup (recommended) backs up email, cloud storage, and other assets within Microsoft Office 365.
Anti-phishing provides scheduled monthly training to and for users as continued protection against evolving threats by teaching caution, awareness, and good email hygiene. Incident response (optional) advanced tools to assist in investigating data breaches from both external and internal sources. Providing litigation holds and forensic research options.
SWFW
Software Firewall
Rule-based client-side firewall runs as software.
Basic application awareness.
Runs in protected mode on the client system.
RCGW
Roaming Client Gateway
Advanced analysis of traffic by the cloud management console.
Advanced application awareness. Extensive database of malicious sites.
Runs in protected mode at the system level on the client system.
WSG
Web Security Gateway
Real-time analysis of all network traffic by the cloud management console.
Protects legacy and otherwise incompatible applications and devices.
Runs as an appliance at the network perimeter to the entire business site.
Advanced Protection
What if something gets through or someone inside the company makes a mistake? We help you implement advanced web monitoring and filtering with the Cisco Umbrella Clients for PCs and laptops. The Cisco Umbrella Client provides advanced web filtering, promotes acceptable use policies, and provides real-time internet protection at the desktop as part of a layered security approach both on and off your business network.
We also help you to implement advanced web monitoring and filtering with Cisco Umbrella Secure Web Gateway for servers and other vulnerable devices. Cisco Umbrella Secure Web Gateway adds advanced threat protection, promotes regulatory compliance, and real-time internet and application protection at the network layer as part of a layered network security approach.
Next, we work with you to implement off-site backups to provide same-day recovery to the same or dissimilar hardware. Cloud and off-site replication are supported. They are the first step to achieving the minimum best practice of the 3-2-1 rule and allow for more robust options, such as 3-2-2, 3-2-3, and others.
PWD
Password
Vulnerable to brute force and other attack modes.
Secured through complexity and frequent changes.
Circumvented by social engineering and poor containment procedures.
MFA
Multi-factor Authentication
Adds layers of protection to your password with software-based keys.
Short-lived challenges to access requests protect against compromise.
Multiple methods for adding security to prevent account lock-outs.
AUTH
Token-Based Authentication
A dedicated device for providing secure keys.
Advanced security keys make passwordless access possible.
Token assignments prevent duplication of software-based keys and tokens.
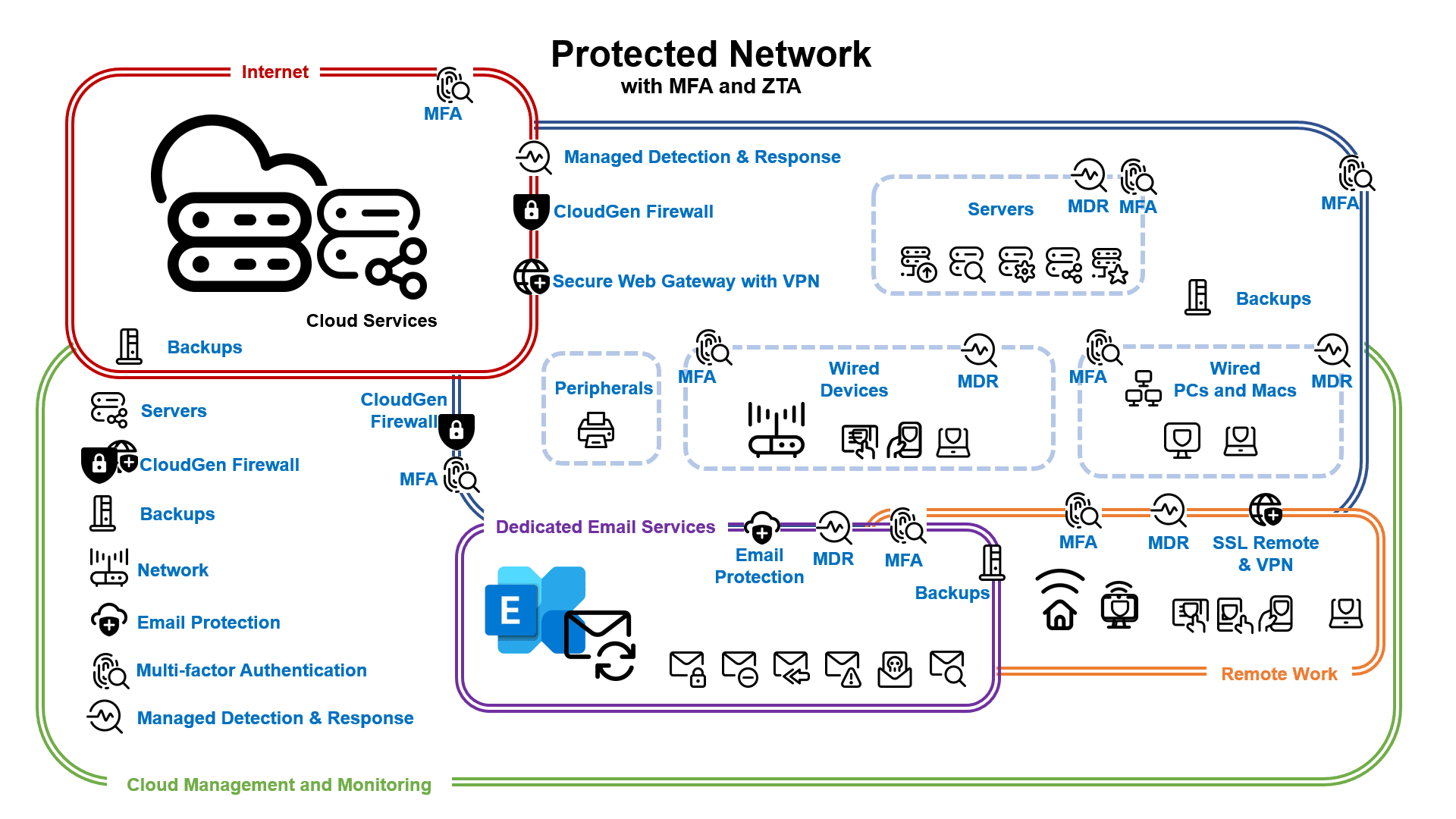
Platinum Protection
Implement BitLocker drive encryption to protect data at rest. Threat actors can steal the data stored on physical devices in many ways. With all the complicated access methods, it can be easy to overlook the basic techniques: physical access, “smash and grab,” or “it just walked away.” However, with Bitlocker, your data is secure and reversibly encrypted, with access keys stored and backed up on your network, making your data secure everywhere.
Next, Exceed Consulting works with vendors to implement an advanced EDR (Endpoint Detection & Response) monitoring solution to protect against network intrusion, permission escalation, unauthorized file modification, unexpected changes in user behavior, unauthorized cloud access to provide real-time monitoring and alerts, report on detected actions, and return forensic detail of monitored systems when needed. This proactive approach ensures you are always one step ahead of potential threats, making you feel prepared and in control of your network security.
The EDR solution provides advanced monitoring and alerting for business-critical data to protect your on-premise and cloud resources against unwanted access, attack, and theft while promoting data security policies.
Platinum Protection with Multi-factor and Zero Trust Architecture
Now that we have discussed threats and methods of protecting your systems let’s discuss how your protective systems are protected.
By implementing a secondary off-site immutable backup solution, you and Exceed Consulting can securely separate your backups, on-site and in the cloud, for a set number of days. Four to seven days is the industry minimum range for off-site backups. These are standard but protected backups on local on-premise storage and the remote repository. Immutable backup jobs are critical to providing security and durability to your primary and off-site backups.
Then, we help protect your user accounts directly by implementing multi-factor or two-factor authentication (MFA or 2FA). Multi-factor authentication eliminates password sharing by requiring a time-based code after entering the password, called a one-time password (OTP). While password theft is always a concern, MFA reduces the risk of attackers gaining password access. When passwords become compromised, MFA prevents attackers from accessing company resources further.
Modern integrated MFA solutions even allow users to manage passwords by resetting lost or forgotten passwords through a mobile application. Meanwhile, MFA offers secure single sign-on with multiple on-premise and cloud services for on-premise and remote workers.
Client-to-Site
VPN
End-user
Provides secure connection between remote computers and your business network.
Software-based VPN for client devices.
Available for PC, Desktop and laptop, Mac, smartphones, and tablets.
Site-to-Site
VPN
Business
Provides a dedicated secure connection between firewalls.
Provides secure fail-over routing to remote and cloud resources over multiple connection types.
Connects Next Generation and Cloud Generation devices.
Multi-Site and Cloud
VPN
Enterprise
Protects site-to-site, cloud-to-cloud, and cloud-to-site traffic.
Prevents internet-based man-in-the-middle attacks.
Protects cloud resources in Amazon AWS, Google Cloud Platform, Microsoft Azure, and more.
Leading us to the final and perhaps most critical stage of implementing a comprehensive Zero Trust Network. The Zero Trust Architecture (ZTA) paradigm emphasizes continuous authentication, least privilege access, and resource-centric security – a powerful approach for safeguarding today’s highly dynamic and interconnected digital environments. By shifting the security focus from the traditional network perimeter to a user- and asset-centric model, ZTA provides organizations with a robust framework to mitigate the evolving threats posed by the modern threat landscape.
However, while Zero Trust Architecture (ZTA) offers a compelling security model, organizations must be prepared to address several challenges to realize its full potential. Successful ZTA implementation requires strategic planning, comprehensive education and training programs for IT teams and end-users, and a devotion to adaptability.
As digital infrastructures and user behavior patterns evolve, organizations must remain agile and vigilant in adapting their Zero Trust Architecture (ZTA) strategies to maintain robust, responsive, and resilient security postures. With the right combination of technological, organizational, and cultural shifts, enterprises can unlock the transformative benefits of ZTA and safeguard their critical digital assets in the face of increasingly sophisticated cyber threats.