
How well do you know email security?
Take a quiz to test your ability to spot email threats.

Take a quiz to test your ability to spot email threats.
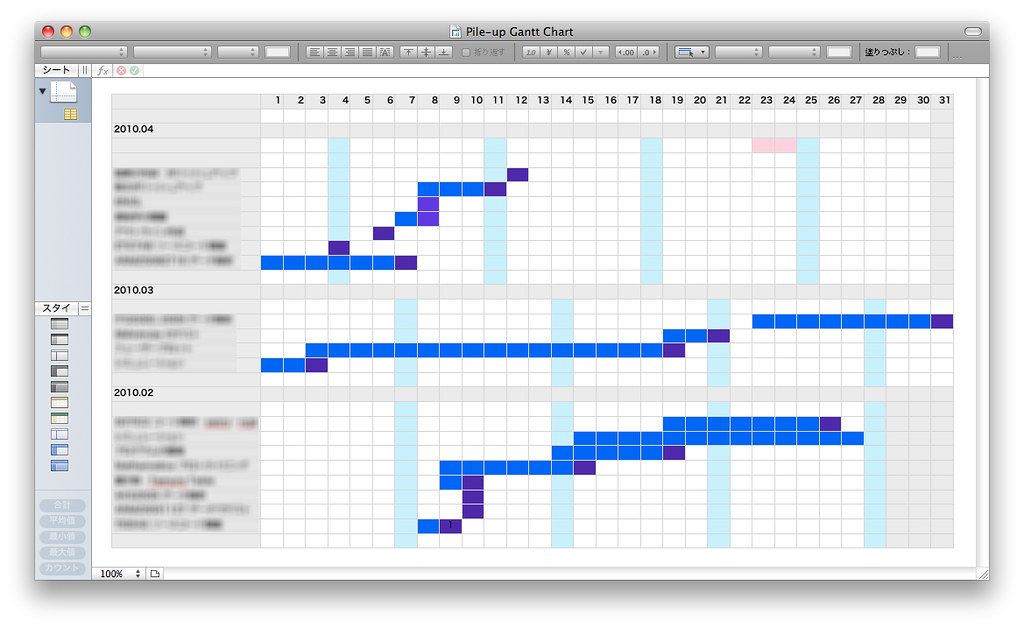
IT project management improves the planning, execution, and oversight of technology-related projects, completing projects on time, within budget, and meeting quality standards by coordinating resources, managing risks, and communicating to achieve goals.
Revolutionize with Cloud Computing. Access powerful resources online; cut costs, boost efficiency instantly.

Unprotected networks are not just a risk; they’re a ticking time bomb. They expose users to cyber threats, data breaches, and costly disruptions. By not implementing advanced security measures, users leave their networks open, inviting in the threats they should guard against. It’s time to transform your network into a fortress, safeguarding your most valuable assets.

Don’t wait. Implement a Zero Trust Network Access to safeguard your business with advanced security. Contact us now to start a future-proof, resilient cybersecurity strategy with Zero Trust Networking. In the cloud-based world, perimeter-based security is insufficient. Cybercriminals evolve – your business can’t afford to be a headline. Zero Trust Architecture provides unparalleled visibility, control, and protection across your digital ecosystem, safeguarding your data, users, and reputation against sophisticated threats.