ID Please
ID Please
Understanding SPF, DMARC, and DKIM.
SPF, DKIM, and DMARC provide protections against forged emails (spoofing), spam, and phishing attempts by verifying senders’ identities and ensuring email integrity.
In today’s digital world, email has become a primary means of communication. However, this convenience also comes with its fair share of risks. Cybercriminals often impersonate others or manipulate emails to deceive recipients into taking harmful actions.
Various email security measures are in place to combat this, including SPF, DMARC, and DKIM. This blog post will demystify these acronyms and explain how they help keep your inbox safe.
Key Terms
- SPF – Sender Policy Framework
- DKIM – DomainKeys Identified Mail
- DMARC – Domain-based Message Authentication, Reporting & Conformance
- Email and Email Server
- Spam Filter
- DNS – Domain Name System
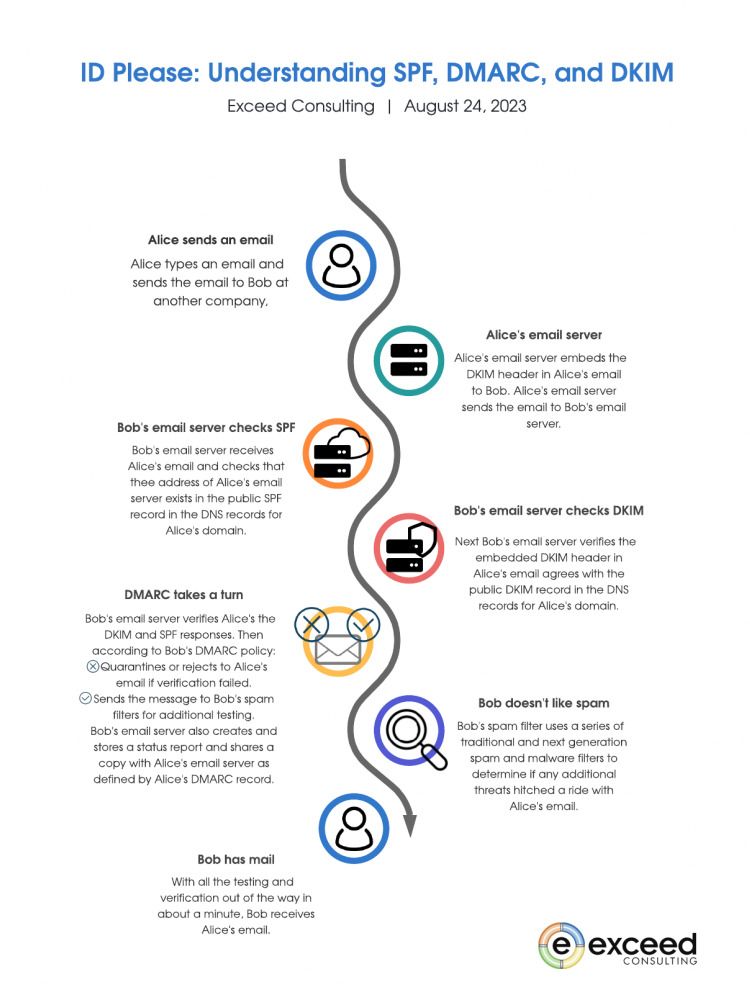
1. SPF (Sender Policy Framework)
Imagine you’re hosting a party and only want invited guests to enter. At the entrance, the security guard checks each guest’s ID against the guest list before granting them access. Similarly, SPF verifies that an email originates from an authorized server by comparing its IP address with the approved list.
Similarly, when you send an email, SPF acts as a personal reference for your email server, ensuring that only “authorized” servers can send emails on behalf of your domain. SPF helps the recipient’s servers validate the authenticity of incoming emails by creating a list of approved IP addresses in the email domain’s DNS records.
SPF helps verify that an email is sent from an authorized server. It works by comparing the IP address of the email server with a list of allowed IP addresses specified in the domain’s DNS records. If the IP address doesn’t match, SPF can mark it as suspicious or reject it.
2. DKIM (DomainKeys Identified Mail)
DKIM adds an extra layer of protection by digitally signing outgoing emails from your domain. This DKIM signature acts as a tamper-proof seal that guarantees the message’s integrity and authenticity throughout transit.
Consider DKIM like sealing an envelope with your unique stamp before sending it off. When you receive a letter with a uniquely sealed envelope, it assures you that nobody accessed or modified the contents during transit. Likewise, when an email arrives with a valid DKIM signature, it confirms that the message hasn’t been tampered with along its journey.
DKIM adds a digital signature to outgoing emails to ensure the sender’s authenticity and integrity. This signature verifies that the message hasn’t been altered during transit and comes from an authorized sender. When receiving an email, servers can check this signature against a public key provided in the domain’s DNS records.
3. DMARC (Domain-based Message Authentication, Reporting & Conformance)
DMARC acts as the supervisor for both SPF and DKIM to provide better visibility into how your domain handles email. It helps prevent email-based fraud by instructing recipient servers on how to treat incoming messages that fail SPF or DKIM validation.
In simpler terms, DMARC ensures that your security guards (SPF) and sealed envelopes (DKIM) are working together effectively. It instructs recipient servers to either reject, quarantine, or deliver an email based on the results of SPF and DKIM checks, giving you control over the handling of suspicious emails.
Think of DMARC as an umbrella policy that helps determine what should happen when suspicious emails are detected: whether they should be put aside for further inspection or rejected outright.
DMARC builds upon SPF and DKIM to provide additional security against phishing and spoofing attacks. With DMARC, organizations can specify the actions to take if an incoming email fails both SPF and DKIM checks – either quarantine or reject it altogether.
To summarize, SPF checks if the email sender is using an authorized server; DKIM verifies the integrity and authenticity of outgoing messages through digital signatures; DMARC sets policies on handling emails that fail both SPF and DKIM checks.
Together, these safeguards help protect against forged emails, spam, and phishing attempts by verifying senders’ identities and ensuring email integrity.