Security & Recovery
Is your business prepared for a disaster?
If you are looking for a disaster recovery specialist, you don’t need to look further. Exceed Consulting provides the knowledge and skills to prepare your company for any disaster. We offer protection for on-premise servers, desktops, mobile devices, and cloud services. Our experts are ready to guide you through the process of building a Disaster Recovery Plan for your business.

Small and mid-sized businesses are the highest risk groups for catastrophic data loss. Regrettably, data loss occurs far too often. Drives fail, and backups could miss an important document. However, when a critical number of files are lost or destroyed, catastrophe can strike unexpectedly. With the help of our automatic online backup and targeted recovery services, your business can avoid this misfortune.
“The U.S. National Cyber Security Alliance found that 60 percent of small companies are unable to sustain their businesses over six months after a cyber-attack.”
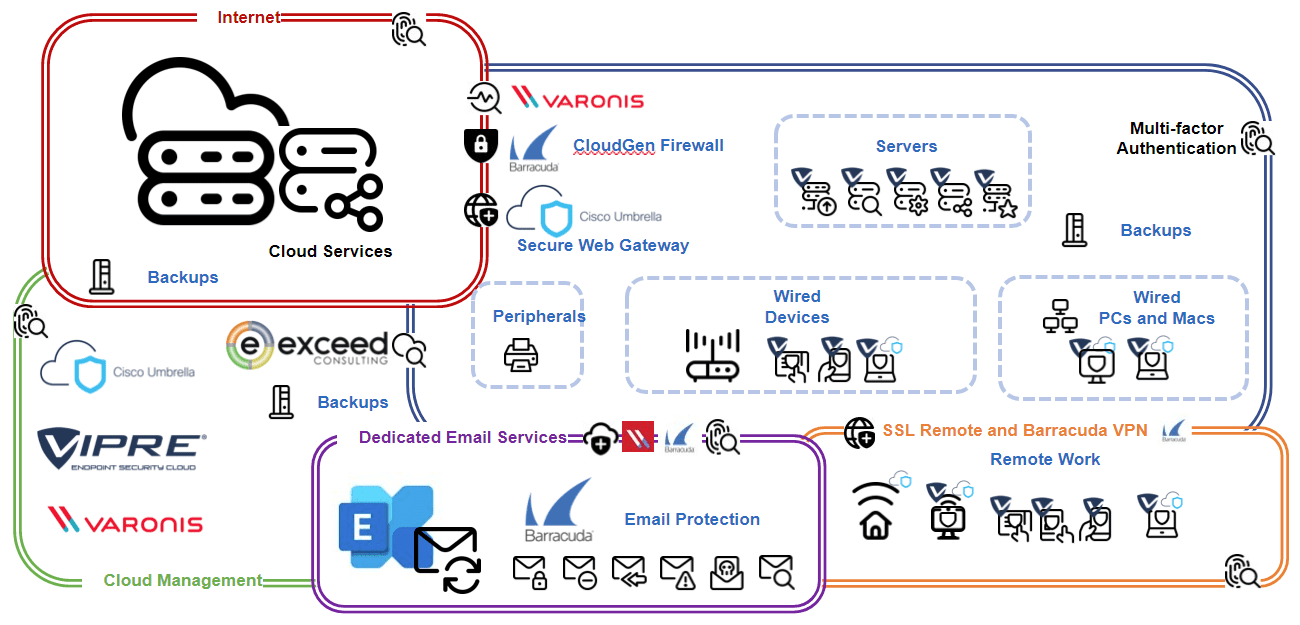
Exceed’s data protection services are a complete set of business continuity tools designed to meet your company’s needs. Your Business Continuity plan is protected with Barracuda Total Email Protection, Vipre, Veeam, Storagecraft, and Synology.
- Business continuity design
- Disaster recovery planning
- Secure remote backup
- Perimeter security
- Email protection and archiving
- Hardware and software monitoring
- Restore business services quickly
Avoiding downtime is an equally significant portion of any business continuity package. Protection of email services and backup of mailboxes assures consistent access during times of crisis.
Adding a layered approach to security through advanced threat detection and next-generation firewall products helps to further your full-service protection.
Exceed data protection services are built and configured to meet your business needs – from desktop to server and mobile platforms to cloud services. With backup solutions for:
- Windows Server (2000 and newer)
- Windows desktops (XP and newer)
- Linux (Red Hat, CentOS, Suse, and Ubuntu)
- Virtual machines (VMware, Hyper-V, and several others)
- Physical servers and desktops
Reliable storage and transfer of your backups are critical parts of the process. We have you covered with industry-leading NAS Storage solutions to fit your needs.
Fire, natural disasters, security flaws, viruses, other malware, or even human error can interrupt your business operations. Maintaining a healthy, resilient network requires a well-designed and properly implemented solution.
Developing your business continuity plan should include determining the recovery time objective (RTO) or the maximum reasonable amount of time your applications can be offline.
A recovery point objective (RPO) is the maximum allowable length of time between snapshots of your data. This period varies based on the nature of your data. Your business-critical information would typically require more frequent images, while slow-moving archival data would not require backups as often. Note that data sizing is not the purpose of RTO and RPO.
The key point behind RTO and RPO calculation is to balance downtime, the complexity of recovery operations, storage footprints, and overall cost to meet your business continuity requirements.
Designing your disaster recovery plan according to your recovery goals, from minor mistakes to catastrophes, requires:
- Clear definition of tasks
- Implementation of controls and secure access
- Up to date software and hardware licensing
- Regular maintenance and patch management
- Setting realistic goals and expectations
- Setting practical recovery paths for your systems
- Understanding the bearing your design has on operations
- Regular testing of the parts, as well as the whole
Contact us to discuss pricing for online backup and recovery pricing, and let’s begin your business continuity discussion today.
Is Your Security Changing Fast Enough?
How well can your business deter attempts from the ever-changing risk of Ransomware attacks? As the Ransomware attacks continue to increase, especially targeting individuals and organizations that are easy to attack, it becomes essential to find adequate protection from these rapidly growing malware attacks. Business owners must pay attention to both their internal systems and the external security of their organizations in a proactive way. The best way to prevent Ransomware attacks is prevention by creating and maintaining a solid yet secure network that can withstand the assault of these malicious programs while reinforcing recovery with immutable backups.
Gone are the days of simply deploying Firewall and Endpoint solutions and feeling comfortable you have done enough. Security has evolved to a security model integrating traditional and next-generation components. In its simplest form, Firewall, Endpoint, DNS (Domain Name Service) protection, Secure Web Gateway, Immutable Backup, and up to and including an Endpoint Detection and Response and Extended Detection and Response solutions. (EDR/XDR) Additionally, we recommend a complete automated file-access monitoring and data protection solution for on-premise and cloud applications of our Healthcare and Financial customers.
A ransomware attack can be one of the most devastating events to a business and can have a long-lasting impact. The best way to protect your business from ransomware attacks is by implementing an EDR (Endpoint Detection & Response) solution. An EDR solution will detect attempts from ransomware and stop them before significant damage occurs. We implement backups of all your data, so you don’t lose anything in the event of a ransomware attack.
Ransomware attacks are a severe threat to any business. The attackers usually demand payment for the decryption key to unlock the computer system and return it to its original state. The best way to protect against ransomware attacks is by having a backup of your data to stand beside your security and allowing you to restore your data from the backup without losing anything.
Reduce yout blast radius.
- Open access remediation
- Zero Trust data security
- Data access governance
Detect & stop threats.
- Ransomware
- Advanced Persistent Threat (APT)
- Insider threats
Streamline compliance.
- Data classification
- Privacy regulation auditing
- Automated Data Subject Access Requests (DSAR)
Ransomware attacks are becoming more and more prevalent, and businesses need to be able to protect themselves against them. Companies should have a plan for when a ransomware attack occurs, and they should have backups of all their data and offsite backups or cloud storage that they can use to recover from the attack. They should also make sure that they are compliant with all the necessary security standards, such as having an up-to-date firewall and antivirus software on their network.
EDR and XDR are essential for businesses to protect themselves against ransomware by ensuring that they have the latest versions of antivirus software installed on their networks. EDR is becoming a requirement to maintain compliance with cyber insurance. Adding EDR to your security arsenal will help protect you from malware and phishing attacks which could lead to a ransomware attack.