Filter your browsing content
Many firewalls, including Barracuda NextGen Firewalls, provide web content filtering from harmful sources. Stand-alone web filters are available as hardware and software if you already have a good firewall. We can assist you in implementing solutions with Cisco Umbrella, Barracuda Web Security, and others.
Use Protection
Get yourself a proper antivirus application. There are many suitable antivirus applications available, some are better than others, and some provide a better fit for your needs and budget. BitDefender, Avira, AVG, and Avast all work well, but we rely on the end-to-end protection of VIPRE on a daily basis.

Be aware
Don’t click on links or attachments in your email. Especially important if the sender appears to be you or someone you know that wouldn’t be sending this material. Just click the delete button. Fake invoices and shipping notifications are standard attachments used to trick you into infecting your computer.
Disable preview mode. Email applications like Outlook, Thunderbird, eM Client, and others often automatically load attachments for your convenience – this loading process can automatically launch a virus. Contact us if you need assistance disabling preview in your email program.
Take a look
What do you do if you receive an email that seems fishy, but you were expecting a message from the person or company? Copy part of the message that doesn’t contain links into the search box at https://www.google.com/ Scammers and spammers love to reuse text; this can benefit you in detecting their tricks. The search results should return many examples of other spam attempts, but don’t click the links in the search results.
Be cautious
If the email seems unusual, especially if it is a company you do business with, the email is probably fake. Scammers and spammers often use trusted addresses to gain access to your PC.
Businesses should never request sensitive information via email. Even if they make such a request, be smarter than them and don’t use email to transfer sensitive data like passwords.
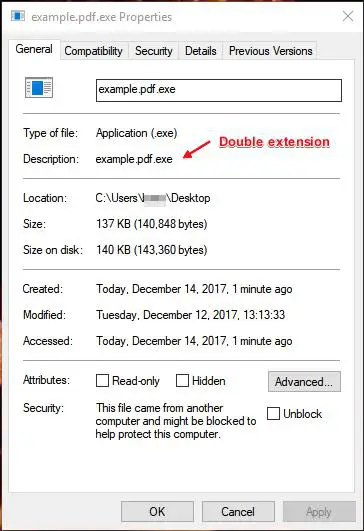
Don’t double-up
Watch out for files with a double extension. Examples: something.txt.vb or other.jpg.exe. By default, Windows usually hides common file extensions, meaning that a program like Paint.exe will appear to you as Paint. Double extensions exploit this by hiding the second, dangerous extension and misleading you with the first (meaningless) extension. You can verify the full name with all extensions by right-clicking on the file, selecting Properties, and looking for the complete file name.
To make file extensions visible, find Folder Options in your Control Panel. (Note that it may be tucked away in Appearance and Personalization or something to that effect.) Under the View tab, please scroll down to Hide Extensions for Known File Types and make sure it is unchecked.
Drive safely
Be careful when using USB drives. Just as an actual virus can jump from person to person, the install process and handshake used to connect a USB drive to a PC can transfer a virus to or from a PC to spread. Most antivirus programs can check USB drives when they connect; please let the antivirus scans run and complete. Please never plug in a USB drive or flash card you don’t trust or “just found somewhere.”
Stop with all the pop-ups
Pop-ups aren’t just annoying; they can often be misleading and dangerous. The primary concern is when a pop-up starts an installation process or mimics a known and trusted application. Rather than trusting the pop-up, contact your system administrator and close the window. Do not click OK, Apply, Continue, or whatever button the pop-up asks you to click. Start a full scan for viruses while you or your system administrator investigate. Better safe than sorry.
An ounce of prevention
Your protection is excellent, but what if you make a mistake? First, it is better to have a message re-sent than getting an infection. Web filters, antivirus, and anti-malware tools catch most malware that fools the human eye. Contact us today to build your layered solution with VIPRE, Cisco, and Barracuda protection.
Plan B (for Backup)
So you did all this, and something still got through – now what?!? Time to pull out the backups. Before getting infected, ensure you have a reliable backup solution, appropriately scheduled and ready to recover. Your system administrator can assist you with configuring and testing your backup solution.
